Access Control Policy Template Nist
Access Control Policy Template Nist - The risk management strategy is an important factor in. Ensure secure access to your organization's information systems with controlcase's access control policy and procedures template. Download for free our comprehensive access control policy template to establish robust measures, ensuring the security of your data. Ac model templates for specifying models/polices: Access control policies, models, and mechanisms. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Access control policies, models, and mechanisms. Organizations planning to implement an access control system should consider three abstractions: Access control policy and procedures address the controls in the ac family that are implemented within systems and organizations. An access control policy defines how your organization manages user access to systems, data, and applications. Ensure secure access to your organization's information systems with controlcase's access control policy and procedures template. The risk management strategy is an important factor in. Composition of multiple ac models into a composed one, e.g., combine rbac with mls. Access control policies, models, and mechanisms. Integrated protectionprotect your appsprotect sensitive infozero trust security Quick to downloadcomprehensive documents30 day gurantee Download for free our comprehensive access control policy template to establish robust measures, ensuring the security of your data. Download our editable, customizable policy documents today. Acpt provides (1) gui templates for composing ac policies, (2) property checking for ac policy models through an symbolic model verification (smv) model checker,. Organizations planning to implement an access control system should consider three abstractions: Ensure secure access to your organization's information systems with controlcase's access control policy and procedures template. Composition of multiple ac models into a composed one, e.g., combine rbac with mls. Policy template guide nist function: Access control policy and procedures address the controls in the ac family that are implemented within systems and organizations. Integrated protectionprotect your appsprotect sensitive infozero. Policy template guide nist function: Acpt provides (1) gui templates for composing ac policies, (2) property checking for ac policy models through an symbolic model verification (smv) model checker,. The risk management strategy is an important factor in. Download now to meet the requirements of iso. Composition of multiple ac models into a composed one, e.g., combine rbac with mls. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. An access control policy defines how your organization manages user access to systems, data, and applications. Integrated protectionprotect your appsprotect sensitive infozero trust security Quick to downloadcomprehensive documents30 day gurantee Access control policy and procedures address the controls in the ac family. Policy template guide nist function: Organizations planning to implement an access control system should consider three abstractions: Composition of multiple ac models into a composed one, e.g., combine rbac with mls. The risk management strategy is an important factor in. Integrated protectionprotect your appsprotect sensitive infozero trust security Access control policies, models, and mechanisms. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. An access control policy defines how your organization manages user access to systems, data, and applications. Composition of multiple ac models into a composed one, e.g., combine rbac with mls. Policy template guide nist function: Download now to meet the requirements of iso. Organizations planning to implement an access control system should consider three abstractions: Organizations planning to implement an access control system should consider three abstractions: Access control policies, models, and mechanisms. The risk management strategy is an important factor in. An access control policy defines how your organization manages user access to systems, data, and applications. Policy template guide nist function: Download our editable, customizable policy documents today. Ac model templates for specifying models/polices: The risk management strategy is an important factor in. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Use this template to simplify the process of developing a nist csf 2.0. The risk management strategy is an important factor in. Access control policy and procedures address the controls in the ac family that are implemented within systems and organizations. Ensure. Download now to meet the requirements of iso. Access control policies, models, and mechanisms. Access control policies, models, and mechanisms. Ac model templates for specifying models/polices: The risk management strategy is an important factor in. Ensure secure access to your organization's information systems with controlcase's access control policy and procedures template. Integrated protectionprotect your appsprotect sensitive infozero trust security The risk management strategy is an important factor in. Download now to meet the requirements of iso. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Access control policies, models, and mechanisms. Organizations planning to implement an access control system should consider three abstractions: Composition of multiple ac models into a composed one, e.g., combine rbac with mls. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Download our editable, customizable policy documents today. Download for free our comprehensive access control policy template to establish robust measures, ensuring the security of your data. Access control policy and procedures address the controls in the ac family that are implemented within systems and organizations. The risk management strategy is an important factor in. Acpt provides (1) gui templates for composing ac policies, (2) property checking for ac policy models through an symbolic model verification (smv) model checker,. Use this template to simplify the process of developing a nist csf 2.0. Ac model templates for specifying models/polices: Policy template guide nist function: Quick to downloadcomprehensive documents30 day gurantee Download now to meet the requirements of iso. Organizations planning to implement an access control system should consider three abstractions:TEMPLATE Information Security Access Control Policy PDF Information
Nist 800 171 Access Control Policy Template Template 1 Resume
ISO 27001 Access Control Policy Ultimate Guide [+ template]
Nist Remote Access Policy Template prntbl.concejomunicipaldechinu.gov.co
Nist 800 53 Access Control Policy Template
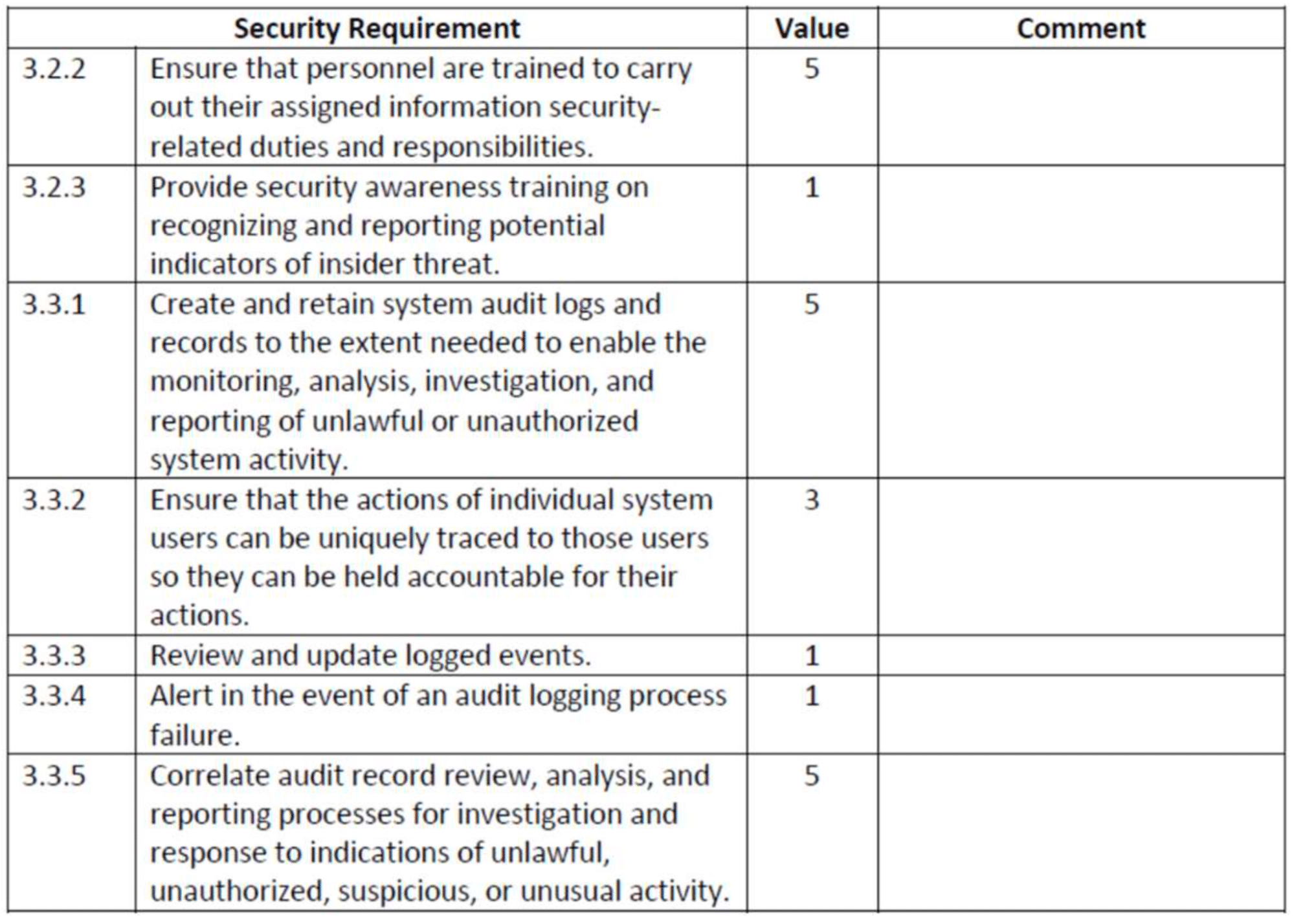
Policy Template Guide NIST Cybersecurity Framework PDF Security
Cybersecurity Access Control Policy Template Developed With NIST
Nist 800171 Access Control Policy Template
Access Control Policy & Procedures Template [w/ Examples]
NIST 800171 Compliance Submission SSE
An Access Control Policy Defines How Your Organization Manages User Access To Systems, Data, And Applications.
Integrated Protectionprotect Your Appsprotect Sensitive Infozero Trust Security
Ensure Secure Access To Your Organization's Information Systems With Controlcase's Access Control Policy And Procedures Template.
Access Control Policies, Models, And Mechanisms.
Related Post:

![ISO 27001 Access Control Policy Ultimate Guide [+ template]](https://hightable.io/wp-content/uploads/2021/04/ISO27001-Access-Control-Policy-Template-Example-1-722x1024.png)





![Access Control Policy & Procedures Template [w/ Examples]](https://ipkeys.com/wp-content/uploads/2023/02/access-control-policy.jpeg)