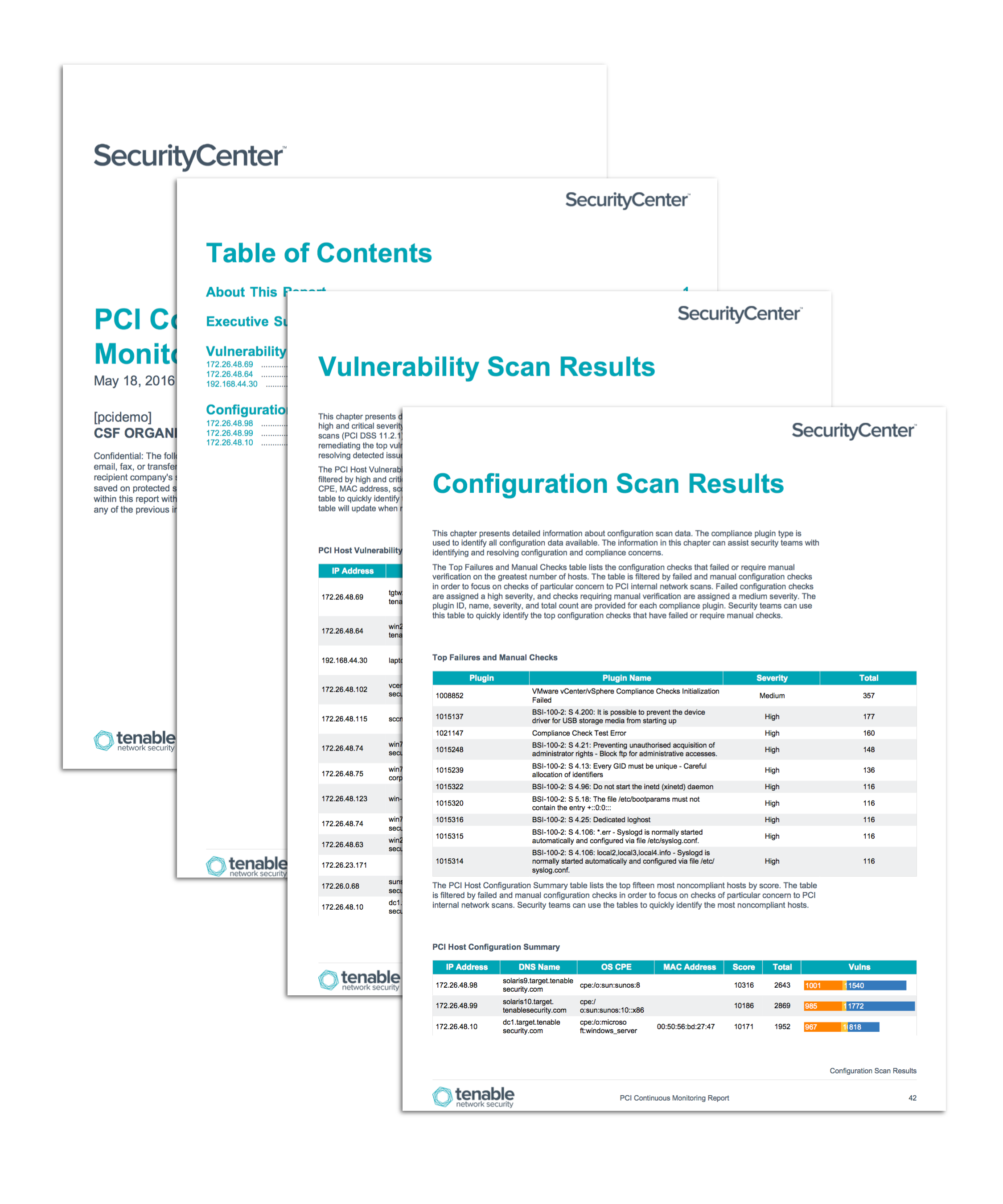
Continuous Monitoring Plan Template
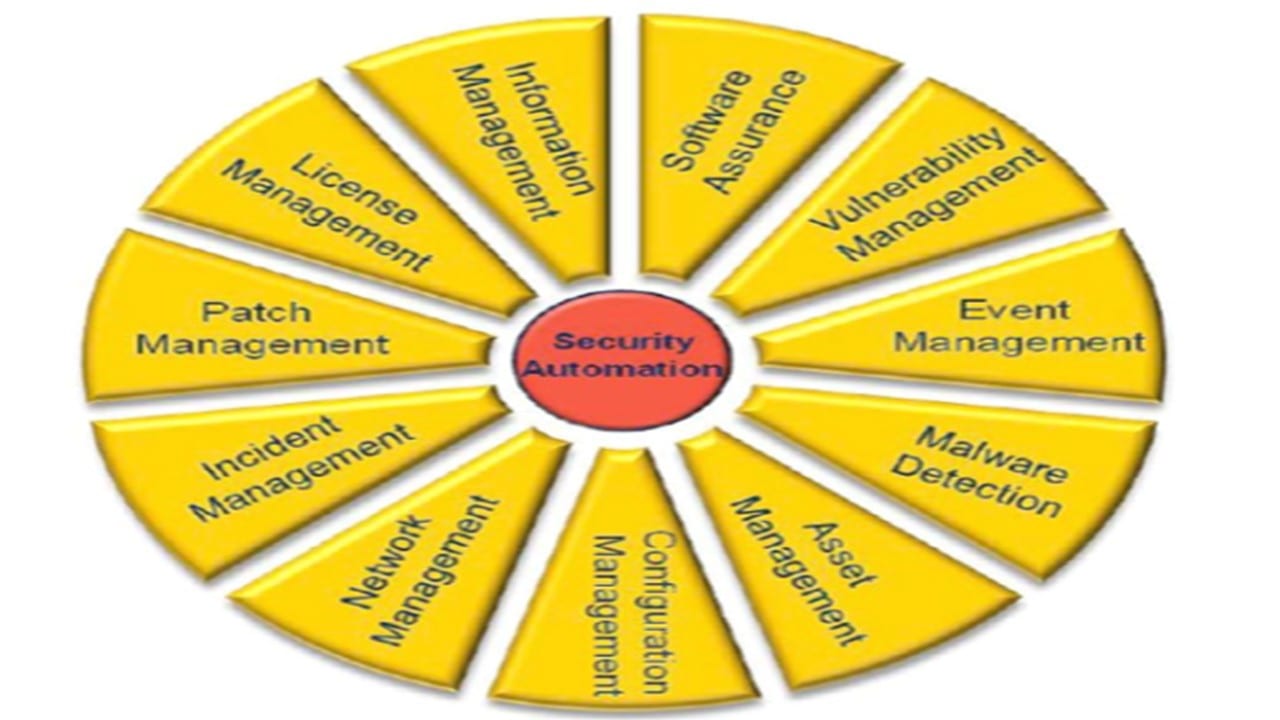
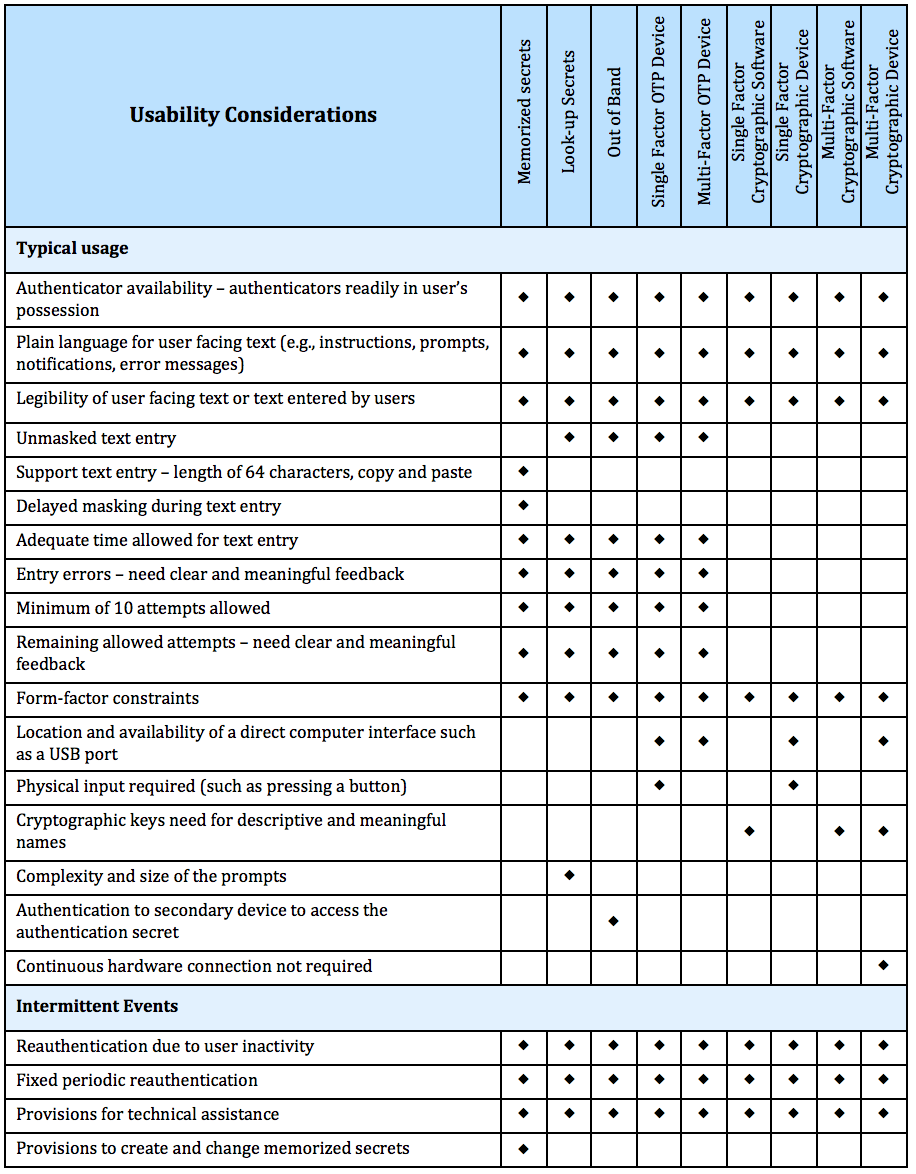
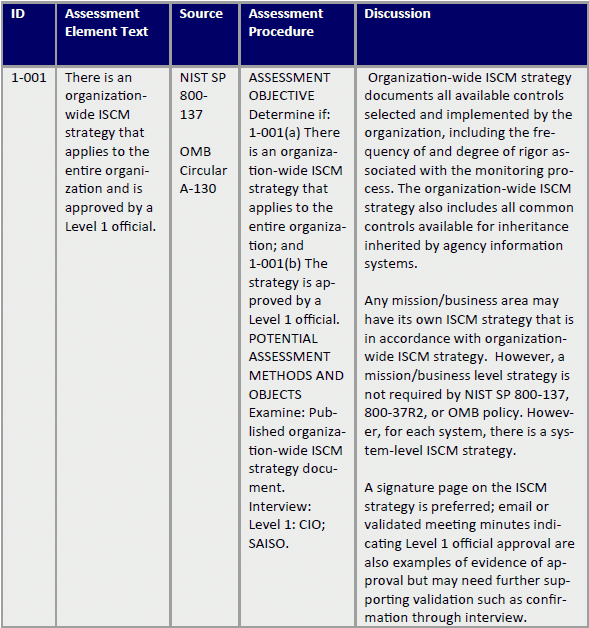
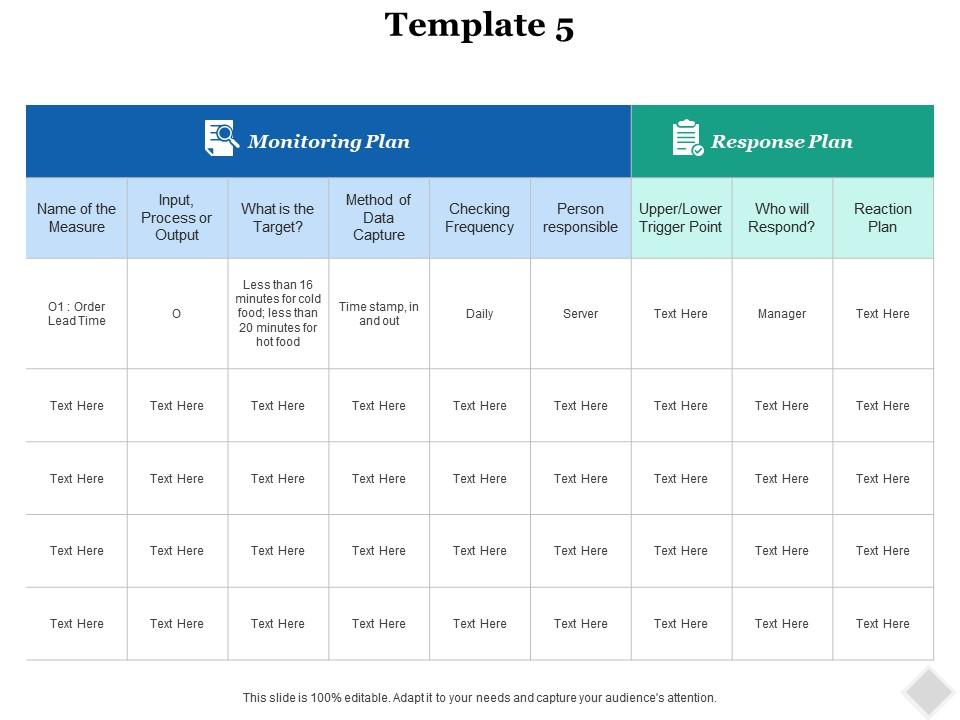
Continuous Monitoring Plan Template - Consistent, comparable, and repeatable approach stable, yet flexible documentation format Each agency (there is roughly 100 command/service/agencies) has their own interpretation of continuous monitoring. The careful documentation of both. Implement a continuous monitoring program to collect the security related data required for the defined metrics and measures. How can we control the scope of work needed to continuously assess the full catalog of security controls?. The project monitoring and control plan provides a structured approach to track, assess, and manage all project elements, ensuring alignment with organizational goals, timelines, budgets,. Establishing a postoperative care plan is an integral aspect of nursing practice and must include everything a patient needs for optimal recovery while mitigating potential. The only part you will have to create is the spreadsheet of monitored controls based upon your. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program. By implementing an rmf information security continuous monitoring (iscm) program, organizations will be conducting continuous monitoring to better protect their. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program. The only part you will have to create is the spreadsheet of monitored controls based upon your. Continuous monitoring strategy guide describes the activities, deliverables, and actors (csp or 3paos) who are required to meet these conmon goals. The successful implementation of a bim execution plan is an iterative process that relies heavily on adaptation and continuous learning. Each agency (there is roughly 100 command/service/agencies) has their own interpretation of continuous monitoring. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso) designated document repository for the ao's review. An effective continuous monitoring plan (plan) can substantially reduce the national environmental satellite, data, and information service (nesdis) costs and level of. By implementing an rmf information security continuous monitoring (iscm) program, organizations will be conducting continuous monitoring to better protect their. This publication describes an example methodology for assessing an organization’s information security continuous monitoring (iscm) program. Section 3 of this document provides a recommended process that agencies should use to monitor conmon performance for csos with a fedramp agency authorization and recommended. Establishing a postoperative care plan is an integral aspect of nursing practice and must include everything a patient needs for optimal recovery while mitigating potential. By implementing an rmf information security continuous monitoring (iscm) program, organizations will be conducting continuous monitoring to better protect their. Data collection methods in six sigma. Each agency (there is roughly 100 command/service/agencies) has their. Automate collection, analysis and reporting of. The successful implementation of a bim execution plan is an iterative process that relies heavily on adaptation and continuous learning. Provider templates stateramp™ is a 501(c)(6) nonprofit membership. An effective continuous monitoring plan (plan) can substantially reduce the national environmental satellite, data, and information service (nesdis) costs and level of. This template summarizes what. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program. Establishing a postoperative care plan is an integral aspect of nursing practice and must include everything a patient needs for optimal recovery while mitigating potential. An effective continuous monitoring plan (plan) can substantially reduce the. The project monitoring and control plan provides a structured approach to track, assess, and manage all project elements, ensuring alignment with organizational goals, timelines, budgets,. Section 3 of this document provides a recommended process that agencies should use to monitor conmon performance for csos with a fedramp agency authorization and recommended. Six sigma projects employ various data. This template summarizes. This presentation covers the nist p… The only part you will have to create is the spreadsheet of monitored controls based upon your. By implementing an rmf information security continuous monitoring (iscm) program, organizations will be conducting continuous monitoring to better protect their. Six sigma projects employ various data. This publication describes an example methodology for assessing an organization’s information. An effective continuous monitoring plan (plan) can substantially reduce the national environmental satellite, data, and information service (nesdis) costs and level of. By implementing an rmf information security continuous monitoring (iscm) program, organizations will be conducting continuous monitoring to better protect their. Data collection methods in six sigma. Implement a continuous monitoring program to collect the security related data required. The careful documentation of both. Provider templates stateramp™ is a 501(c)(6) nonprofit membership. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program. An effective continuous monitoring plan (plan) can substantially reduce the national environmental satellite, data, and information service (nesdis) costs and level of.. The only part you will have to create is the spreadsheet of monitored controls based upon your. Consistent, comparable, and repeatable approach stable, yet flexible documentation format Learn about the concepts, principles, and process of continuous monitoring for federal information systems and organizations. An effective continuous monitoring plan (plan) can substantially reduce the national environmental satellite, data, and information service. Information system continuous monitoring (iscm) plan. Provider templates stateramp™ is a 501(c)(6) nonprofit membership. Learn about the concepts, principles, and process of continuous monitoring for federal information systems and organizations. Continuous monitoring ensures the plan remains effective throughout the project lifecycle. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso) designated document. Start with looking at the specific agencies document. Continuous monitoring ensures the plan remains effective throughout the project lifecycle. Six sigma projects employ various data. Continuous monitoring strategy guide describes the activities, deliverables, and actors (csp or 3paos) who are required to meet these conmon goals. Consistent, comparable, and repeatable approach stable, yet flexible documentation format This publication describes an example methodology for assessing an organization’s information security continuous monitoring (iscm) program. An effective continuous monitoring plan (plan) can substantially reduce the national environmental satellite, data, and information service (nesdis) costs and level of. The only part you will have to create is the spreadsheet of monitored controls based upon your. The careful documentation of both. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso) designated document repository for the ao's review. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program. How can we control the scope of work needed to continuously assess the full catalog of security controls?. The successful implementation of a bim execution plan is an iterative process that relies heavily on adaptation and continuous learning. The project monitoring and control plan provides a structured approach to track, assess, and manage all project elements, ensuring alignment with organizational goals, timelines, budgets,. By implementing an rmf information security continuous monitoring (iscm) program, organizations will be conducting continuous monitoring to better protect their. Start with looking at the specific agencies document. Establishing a postoperative care plan is an integral aspect of nursing practice and must include everything a patient needs for optimal recovery while mitigating potential. Implement a continuous monitoring program to collect the security related data required for the defined metrics and measures. Data collection methods in six sigma. Information system continuous monitoring (iscm) plan. Consistent, comparable, and repeatable approach stable, yet flexible documentation formatTEMPLATE Continuous Monitoring Plan (ConMon) ⋆ The Cyber Sentinel
Rmf Continuous Monitoring Plan Template
Continuous Monitoring Plan Template prntbl.concejomunicipaldechinu.gov.co
Nist Continuous Monitoring Plan Template
Nist Continuous Monitoring Plan Template
Continuous Monitoring Plan Template prntbl.concejomunicipaldechinu.gov.co
Nist Continuous Monitoring Plan Template
Rmf Continuous Monitoring Plan Template
Continuous Monitoring Plan Template
Continuous Monitoring Plan Template
Continuous Monitoring Strategy Guide Describes The Activities, Deliverables, And Actors (Csp Or 3Paos) Who Are Required To Meet These Conmon Goals.
Automate Collection, Analysis And Reporting Of.
Provider Templates Stateramp™ Is A 501(C)(6) Nonprofit Membership.
Learn About The Concepts, Principles, And Process Of Continuous Monitoring For Federal Information Systems And Organizations.
Related Post: