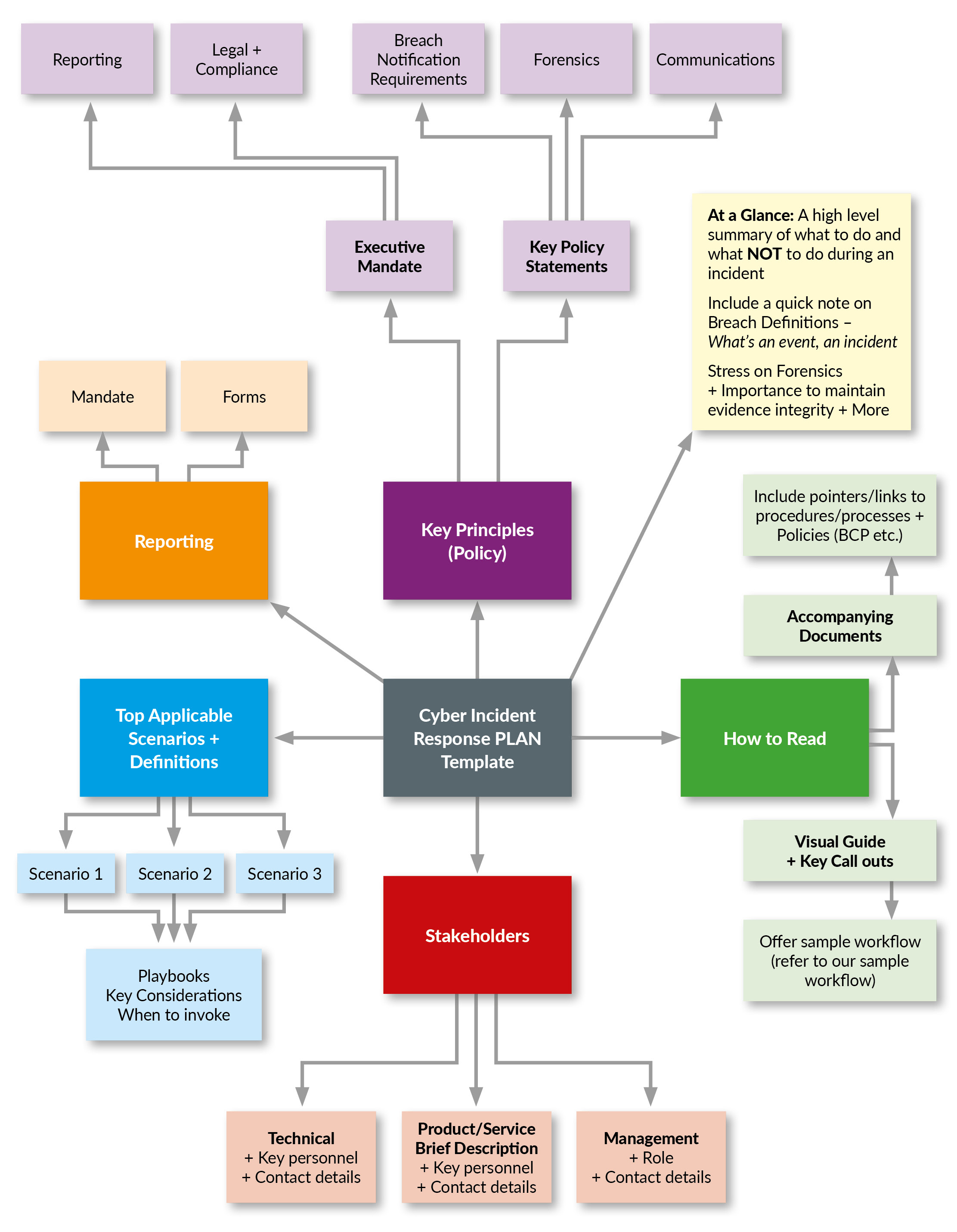
Cyber Incident Response Plan Template Doc
Cyber Incident Response Plan Template Doc - Create your own concise, flexible, and free incident response plan here, based on our compilation of best practices. In addition to nist, there is sans incident. In this article, we look at 12 incident response plan templates you can use to start building a plan that meets your organization's needs. Incident plan response plans are usually used in it enterprises to identify, respond and limit the security accidents as they happen. The ncirp is an essential governance document to guide national resilience and incident response efforts. A strong cybersecurity incident response plan is essential to detect, respond to, and mitigate security breaches efficiently. A broader strategy document, an irp outlines the organization's overall approach to managing cybersecurity threats, focusing on policies and goals. This document provides a cyber security incident response plan template for a company. It is a framework that benefits from cisa’s leadership and expertise. Templates provide a structured format. The plan templates that are available here will help you. What is an incident response plan?. It emphasizes a proactive approach,. In addition to nist, there is sans incident. Secure your digital assets with template.net's cybersecurity incident emergency response plan template. An incident response plan template is a structured approach for identifying, responding to and managing cybersecurity incidents or data breaches. To create such a plan, it is critical to understand potential risks, and one of the best ways to do that is to conduct a proactive threat hunt and compromise assessment. In today’s digital world, cyber threats are on the rise. Cyberspace effects implementation and operation protection and. The response should limit the potential. An incident response (ir) plan is a documented approach to address and manage cybersecurity incidents or attacks. In today’s digital world, cyber threats are on the rise. Simply input your information and press enter to see the. It emphasizes a proactive approach,. It outlines goals for responding to cyber incidents, including protecting data, recovering business. In addition to nist, there is sans incident. This plan details steps for addressing and mitigating cyber threats. An incident response plan template is a structured approach for identifying, responding to and managing cybersecurity incidents or data breaches. 5 steps to building an incident response plan. Execute key portions of a cyber incident response plan after its development; An incident response (ir) plan is a documented approach to address and manage cybersecurity incidents or attacks. An incident response plan template is a structured approach for identifying, responding to and managing cybersecurity incidents or data breaches. To create the plan, the steps in the following example should be replaced with contact information and specific. The ncirp is an essential. Secure your digital assets with template.net's cybersecurity incident emergency response plan template. Create your own concise, flexible, and free incident response plan here, based on our compilation of best practices. 5 steps to building an incident response plan. It emphasizes a proactive approach,. This blog provides ideas on how you can use. In addition to nist, there is sans incident. To create such a plan, it is critical to understand potential risks, and one of the best ways to do that is to conduct a proactive threat hunt and compromise assessment. Simply input your information and press enter to see the. Our free cyber incident response plan template includes: This document provides. A broader strategy document, an irp outlines the organization's overall approach to managing cybersecurity threats, focusing on policies and goals. This plan details steps for addressing and mitigating cyber threats. A cyber security policy template can simplify the process of policy creation. 5 steps to building an incident response plan. It emphasizes a proactive approach,. The plan templates that are available here will help you. In today’s digital world, cyber threats are on the rise. Incident plan response plans are usually used in it enterprises to identify, respond and limit the security accidents as they happen. Secure your digital assets with template.net's cybersecurity incident emergency response plan template. A broader strategy document, an irp outlines. This plan details steps for addressing and mitigating cyber threats. Cyberspace effects implementation and operation protection and. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. What is an incident response plan?. Contact us · security · legal Cyberspace effects implementation and operation protection and. The response should limit the potential. In addition to nist, there is sans incident. This document discusses the steps taken during an incident response plan. It outlines goals for responding to cyber incidents, including protecting data, recovering business. This document discusses the steps taken during an incident response plan. The response should limit the potential. In addition to nist, there is sans incident. Secure your digital assets with template.net's cybersecurity incident emergency response plan template. Incident plan response plans are usually used in it enterprises to identify, respond and limit the security accidents as they happen. It is a framework that benefits from cisa’s leadership and expertise. There are several resources that can help you develop your incident response plan. It emphasizes a proactive approach,. Create your own concise, flexible, and free incident response plan here, based on our compilation of best practices. Incident plan response plans are usually used in it enterprises to identify, respond and limit the security accidents as they happen. The plan templates that are available here will help you. In addition to nist, there is sans incident. In today’s digital world, cyber threats are on the rise. An incident response (ir) plan is a documented approach to address and manage cybersecurity incidents or attacks. This document discusses the steps taken during an incident response plan. This blog provides ideas on how you can use. A broader strategy document, an irp outlines the organization's overall approach to managing cybersecurity threats, focusing on policies and goals. Simply input your information and press enter to see the. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. The ncirp is an essential governance document to guide national resilience and incident response efforts. To create such a plan, it is critical to understand potential risks, and one of the best ways to do that is to conduct a proactive threat hunt and compromise assessment.Cybersecurity Incident Response Plan Template Best Printable Resources
Free Cybersecurity Incident Response Plan Template Develop Your Plan
Cyber Incident Response Form Template in Word, PDF, Google Docs
CMA Cyber Incident Respons Plan Template Public PDF Crisis
The Ultimate Cyber Incident Response Plan (Template Included) — Etactics
Digital Marketing Agency Cybersecurity Incident Response Plan Template
Incident cyber response template plan structure planning immediately
Free Cybersecurity Incident Response Plan Template Printable Templates
Free Cyber Security Policy Template Of 8 Incident Response Plan
Vicgov Cyber Incident Response Plan Template
5 Steps To Building An Incident Response Plan.
Execute Key Portions Of A Cyber Incident Response Plan After Its Development;
Secure Your Digital Assets With Template.net's Cybersecurity Incident Emergency Response Plan Template.
The Response Should Limit The Potential.
Related Post: