Server Side Template Injection
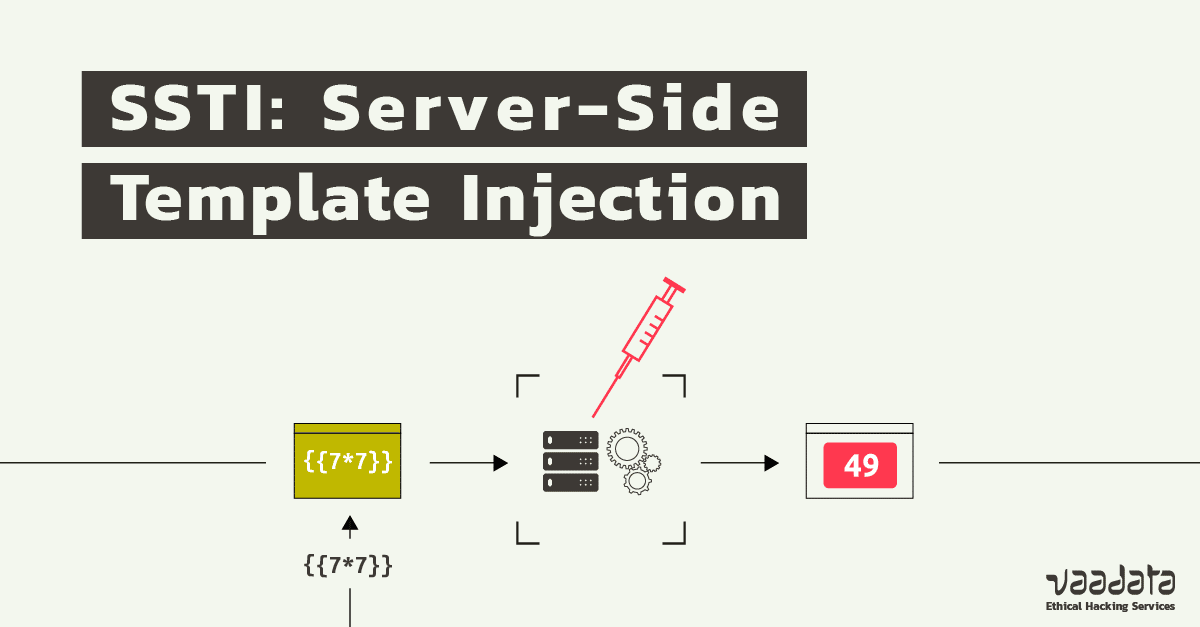
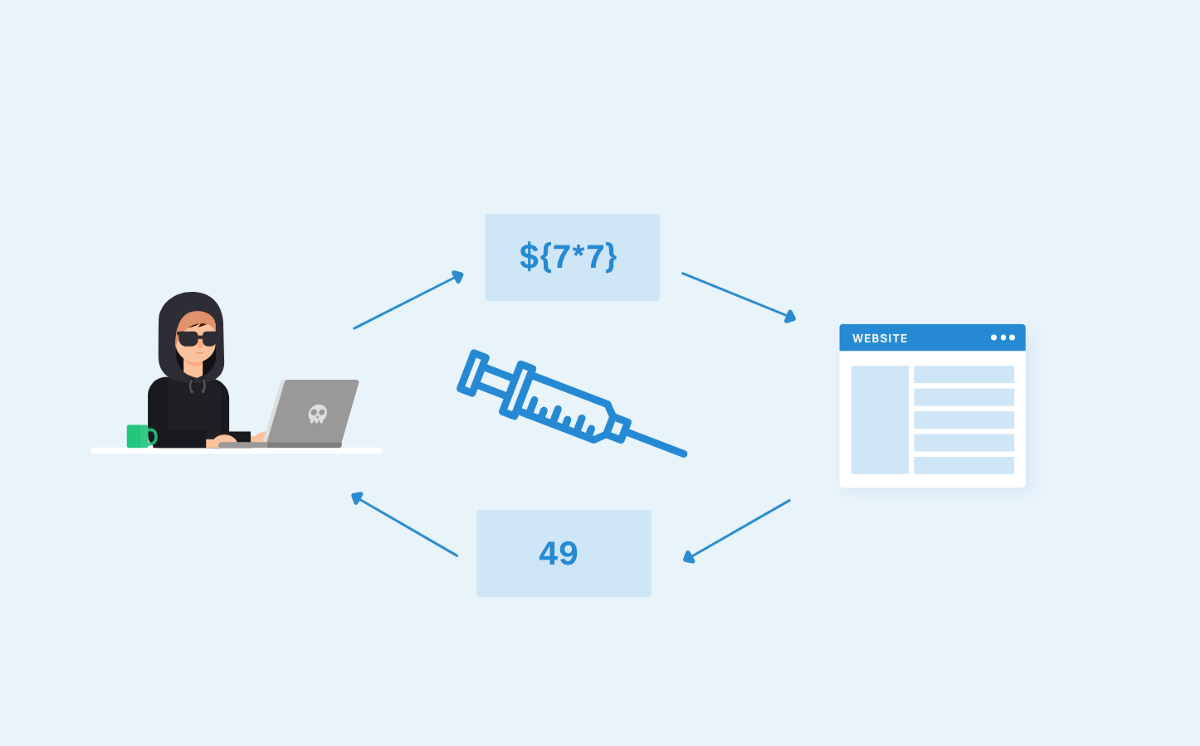
Server Side Template Injection - If an application improperly handles user. See examples of ssti vulnerabilities,. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Understanding the mechanisms, risks, and. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. See examples of ssti vulnerabilities,. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Understanding the mechanisms, risks, and. If an application improperly handles user. If an application improperly handles user. See examples of ssti vulnerabilities,. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Understanding the mechanisms, risks, and. Understanding the mechanisms, risks, and. See examples of ssti vulnerabilities,. If an application improperly handles user. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. If an application improperly handles user. Understanding the mechanisms, risks, and. See examples of ssti vulnerabilities,. Find out how to identify, remediate, and prevent this vulnerability with examples and references. If an application improperly handles user. Find out how to identify, remediate, and prevent this vulnerability with examples and references. See examples of ssti vulnerabilities,. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Understanding the mechanisms, risks, and. See examples of ssti vulnerabilities,. If an application improperly handles user. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Understanding the mechanisms, risks, and. If an application improperly handles user. Understanding the mechanisms, risks, and. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. See examples of ssti vulnerabilities,. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Understanding the mechanisms, risks, and. If an application improperly handles user. Find out how to identify, remediate, and prevent this vulnerability with examples and references. See examples of ssti vulnerabilities,. If an application improperly handles user. See examples of ssti vulnerabilities,. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Understanding the mechanisms, risks, and. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. Find out how to identify, remediate, and prevent this vulnerability with examples and references. See examples of ssti vulnerabilities,. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. If an application improperly handles user. Understanding the mechanisms, risks, and. Find out how to identify, remediate, and prevent this vulnerability with examples and references. See examples of ssti vulnerabilities,. Understanding the mechanisms, risks, and. If an application improperly handles user. Search hacking techniques and tools for penetration testings, bug bounty, ctfs. See examples of ssti vulnerabilities,. If an application improperly handles user. Find out how to identify, remediate, and prevent this vulnerability with examples and references. Understanding the mechanisms, risks, and.Server Side Template Injection Vulnerability Explained TryHackMe SSTI
ServerSide Template Injection how to prevent it
A Pentester’s Guide to Command Injection Cobalt
Serverside template injection Explanation, Discovery, Exploitation
Server Side Template Injection (SSTI) by Eren Sagdic Medium
Understanding ServerSide Template Injection (SSTI) and Its Role in Web
Server Side Template Injection SSTI vulnerability
Server Side Template Injection
SSTI ServerSide Template Injection Guide. • CyberAstral • Trusted
Server Side Template Injection Explanation from the basics and a demo
Search Hacking Techniques And Tools For Penetration Testings, Bug Bounty, Ctfs.
Related Post: